GNAT SAS helps developers gain a deep understanding of their code and build more reliable and secure software systems.
GNAT SAS features an Ada source code analyzer that detects run-time and logic errors. It assesses potential bugs and vulnerabilities before program execution, serving as an automated peer reviewer, helping to find errors easily at any stage of the development life-cycle. It helps you improve the quality of your code and makes it easier for you to perform safety and/or security analysis.
GNAT SAS is a stand-alone tool that runs on Windows and Linux platforms and may be used with any standard Ada compiler or fully integrated into the GNAT Pro development environment. It can detect several of the “Top 25 Most Dangerous Software Errors” in the Common Weakness Enumeration. It supports all versions of Ada (83, 95, 2005, 2012, 2022).
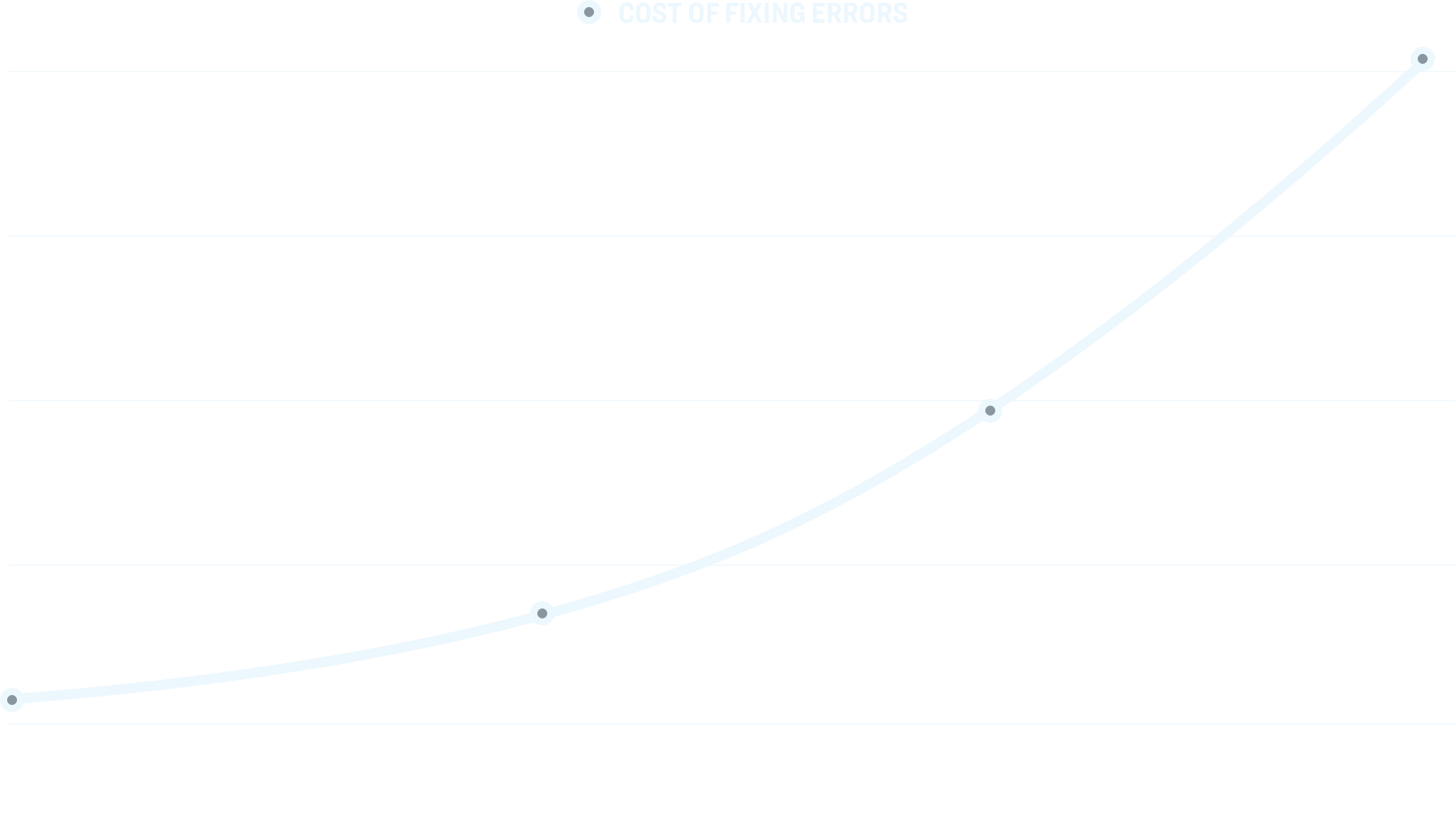
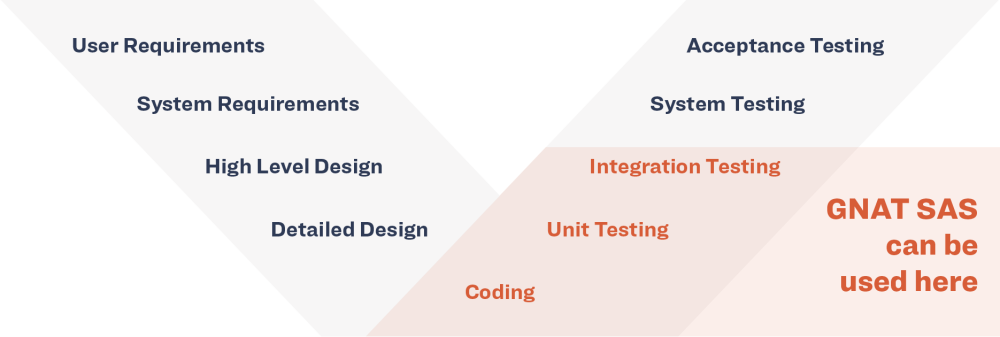
GNAT SAS’s advanced static error detection finds bugs before programs are run. By mathematically analyzing every line of code and considering every possible input and every path through the program, it can be used very early in the development life-cycle to identify problems when they are much less costly to repair. The tool can also be used retrospectively on existing code bases, to detect latent vulnerabilities.
GNAT SAS uses a “bottom-up” approach where each subprogram is analyzed separately, with its effects summarized/propagated for caller analysis. This enables it to scale up to very large applications, and also allows partial analysis (e.g., a library or even a specific unit without the enclosing context) with no need for a driver or stubs. In addition, it can take advantage of multicore architectures to significantly speed up its running time.
GNAT SAS is integrated with GNAT Studio IDE and with a web server for viewing its HTML output. It can also be launched from Jenkins (continuous builder) and integrates with SonarQube via GNATdashboard.
A CWE Compatible Tool
GNAT SAS has been designated as CWE-Compatible by the MITRE Corporation's Common Weakness Enumeration (CWE) Compatibility and Effectiveness Program and can detect a multitude of code weaknesses, including several that are among, or are in the same class as, the CWE’s Top 25 Most Dangerous Software Errors.
It's advanced static error detection finds bugs before programs are run. By mathematically analyzing every line of code, and considering every possible input and every path through the program, It can be used very early in the development life-cycle to identify problems when they are much less costly to repair. The tool can also be used retrospectively on existing code bases, to detect latent vulnerabilities.
CWE-120 (Classic Buffer Overflow)
“The program copies an input buffer to an output buffer without verifying that the size of the input buffer is less than the size of the output buffer, leading to a buffer overflow.”
CWE-131 (Incorrect Calculation of Buffer Size)
“The software does not correctly calculate the size to be used when allocating a buffer, which could lead to a buffer overflow.”
CWE-190 (Integer Overflow or Wraparound)
“The software performs a calculation that can produce an integer overflow or wraparound, when the logic assumes that the resulting value will always be larger than the original value. This can introduce other weaknesses when the calculation is used for resource management or execution control.”
The following CWE weaknesses will also be detected:
| CWE weakness | Description |
|---|---|
| CWE 119, 120, 124, 125, 126, 127, 129, 130, 131 | Buffer overflow/underflow |
| CWE 136, 137 | Variant record field violation, Use of incorrect type in inheritance hierarchy |
| CWE 190, 191 | Numeric overflow/underflow |
| CWE 362, 366 | Race condition |
| CWE 369 | Division by zero |
| CWE 457 | Use of uninitialized variable |
| CWE 476 | Null pointer dereference |
| CWE 561 | Dead (unreachable) code |
| CWE 563 | Unused or redundant assignement |
| CWE 570 | Expression is always false |
| CWE 571 | Expression is always true |
| CWE 628 | Incorrect arguments in call |
| CWE 667 | Improper locking |
| CWE 682 | Incorrect calculation |
| CWE 820 | Missing synchronization |
| CWE 821 | Incorrect synchronization |
| CWE 835 | Infinite loop |
Expert Support
Integral to every one of our products are the consulting and support services we provide to our customers. While every company says they offer excellent support, for us it‘s a critical part of our business model and something we take very seriously.